Group-IB, a global cybersecurity leader headquartered in Singapore, has assisted in the INTERPOL-led Operation Nervone, aimed at successfully disrupting the operations of a cybercriminal syndicate dubbed OPERA1ER by Group-IB (also known as NXSMS, DESKTOP-Group, and Common Raven as named by SWIFT ISAC) in French-speaking Africa.
RELATED: Africa Cyber Surge Operation: Group-IB assists INTERPOL-led operation to combat cybercrime on continent
This initiative took place under the guises of the African Joint Operation against Cybercrime (AFJOC) and the INTERPOL Support Programme for the African Union (ISPA), in conjunction with AFRIPOL, the Direction de L’information et des Traces Technologiques (DITT), Group-IB and the Orange CERT Coordination Center (Orange-CERT-CC). Group-IB’s Threat Intelligence and High-Tech Crime Investigations units, which have tracked OPERA1ER since 2019, provided timely intelligence that uncovered the identity and potential location of a key member of the cybercriminal group, who was subsequently detained in Abidjan, Côte d’Ivoire.
Group-IB, which has a zero-tolerance policy to cybercrime, is a committed, long-standing private sector partner of INTERPOL, and the company is proud of its significant contribution to Operation Nervone. This successful initiative was preceded by the INTERPOL-led Operation Falcon I, Falcon II, and Delilah, which led to the arrests of more than a dozen individuals in Nigeria linked to the transnational phishing syndicate dubbed TMT.
Who are OPERA1ER?
In November 2022, Group-IB’s Threat Intelligence team, along with their partners at the Orange CERT Coordination Center, published OPERA1ER: Playing God without permission, a report detailing the financially motivated attacks of a prolific Francophone threat actor, codenamed OPERA1ER.
The group managed to carry out more than 30 successful attacks against financial institutions, banks, mobile banking services, and telecommunications companies in Côte d’Ivoire, Mali, Burkina Faso, Benin, Cameroon, Bangladesh, Gabon, Niger, Nigeria, Paraguay, Senegal, Sierra Leone, Uganda, Togo, and Argentina between March 2018 and October 2022. OPERA1ER was confirmed to have stolen at least $11 million from their attacks, although the actual damages could be as high as $30 million. Group-IB provided threat intelligence and notifications to the affected companies during the investigation, helping to reduce financial losses.
The group managed to carry out more than 30 successful attacks against financial institutions, banks, mobile banking services, and telecommunications companies in Côte d’Ivoire, Mali, Burkina Faso, Benin, Cameroon, Bangladesh, Gabon, Niger, Nigeria, Paraguay, Senegal, Sierra Leone, Uganda, Togo, and Argentina between March 2018 and October 2022. OPERA1ER was confirmed to have stolen at least $11 million from their attacks, although the actual damages could be as high as $30 million. Group-IB provided threat intelligence and notifications to the affected companies during the investigation, helping to reduce financial losses.
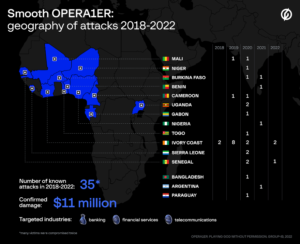
Figure 1: Attack overview of OPERA1ER
OPERA1ER was notable for leveraging off-the-shelf open-source programs and malware freely available on the dark web, and popular red teaming frameworks, such as Metasploit and Cobalt Strike. They launched their attacks by sending high-quality phishing emails that targeted a specific team within an organization. Most of the messages were written in French, and mimicked fake tax office notifications or hiring offers.
OPERA1ER’s core goal was financial gain. The findings of the investigation revealed that OPERA1ER was able to get access to internal payment systems used by the affected organizations, and leveraged this to withdraw funds. In one case studied by researchers, a network of more than 400 subscriber accounts controlled by money mules was used to cash out stolen funds.
United effort
Group-IB’s Threat Intelligence and High-Tech Crime Investigations teams contributed to Operation Nervone by sharing in collaboration with Orange-CERT-CC information on OPERA1ER, identifying the attackers’ infrastructure, analyzing their digital traces and assembling data that uncovered the identity and potential location of a key figure in the organization. The operation also benefited from the efforts from law enforcement and governmental agencies from several INTERPOL member states.
“We have been tracking OPERA1ER since 2019. Any attempt to investigate a sophisticated threat actor such as OPERA1ER, which stole millions from financial service companies and telecom providers across the world, requires a highly coordinated effort between public and private sector bodies. The success of Operation Nervone exemplifies the importance of threat data exchange, and thanks to our collaboration with INTERPOL, Orange-CERT-CC and private and public sector partners, we were collectively able to piece together the whole puzzle. At Group-IB, we are proud of our contribution to Operation Nervone, which is fully in alignment with the company’s strategic mission of fighting against cybercrime in all its forms. Our commitment to this goal remains constant.” Dmitry Volkov, CEO at Group-IB, said. “
“Operation Nervone is a testament to what we can achieve through international collaboration and intelligence sharing. This operation marks a significant step in our ongoing mission to dismantle organized cybercrime networks, showcasing the power of collective action in stemming the tide against cybercrime,” said the INTERPOL Assistant Director of Cybercrime Operations Bernardo Pillot.
COVER IMAGE:Interpol





























