NordLocker analysis shows what businesses have faced ransomware attacks in 2020 and 2021 the most.
Key information and findings:
- A thorough analysis of 1,200 companies hit by 10 infamous ransomware gangs in 2020 and 2021 identified 35 of the most victimized industries.
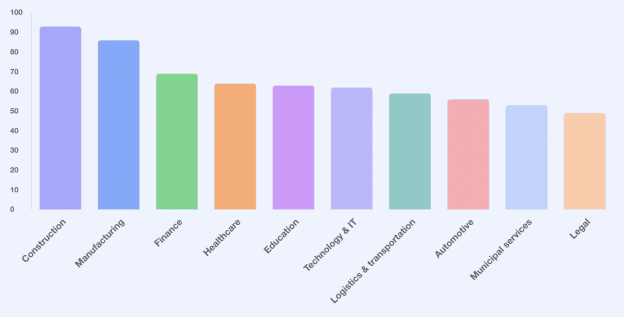
- Construction is the top industry hit by ransomware, followed by Manufacturing. The rest of the top 10 victimized industries are Finance, Healthcare, Education, Technology & IT, Logistics & transportation, Automotive, Municipal services, and Legal.
- The top 10 countries where businesses get attacked most: the US (732 cases), UK (74), Canada (62), France (58), Germany (39), Italy (33), Spain (26), Australia (23), Brazil (16), and Japan (11).
- The most prolific ransomware gangs analyzed in the study are Conti (450 attacks), REvil (210), DopplePaymer (200), and PYSA (188).
More information: https://nordlocker.com/recent-ransomware-attacks/
NordLocker analysis shows what businesses have faced ransomware attacks in 2020 and 2021 the most
The new desk research by NordLocker has discovered which industries are the most popular targets for ransomware gangs to launch their attacks against. After a thorough analysis of 1,200 companies hit by 10 infamous ransomware gangs in 2020 and 2021, 35 of the most victimized industries were identified.
“The latest statistics indicate that a worrying 37% of companies worldwide became victims of ransomware in 2020,” says Oliver Noble, a cybersecurity expert at NordLocker, an encrypted cloud service provider. “From Campari Group in the Food & Beverage industry to Baltimore County public schools in the Education sector, both of which became victims of ransomware last year, no business or institution can feel safe. Our analysis presents the scope of recent ransomware hacks as well as indicates which industries need to stay particularly cautious.”
Top industries hit by ransomware
NordLocker’s analysis reveals that Construction is the top industry hit by ransomware (93 victimized companies), followed by Manufacturing (86). Finance (69 ransomware cases), Healthcare (65), Education (63), Technology & IT (62), Logistics & transportation (59), Automotive (56), Municipal services (52), and Legal (49) are business areas that make the list of the top 10 industries most targeted by ransomware gangs.
Among the hacked companies discovered by NordLocker’s research, there were not only large organizations, such as a global hotel chain, an automotive conglomerate, or a world-wide clothing brand, but also small family-owned and operated businesses like an Italian restaurant or a local dental clinic.
“It is surprising how many companies still take cybersecurity for granted, ‘inviting’ hackers to exploit their vulnerabilities,” says Oliver Noble. “When successfully attacked, companies get all their employee data, customer details, client agreements, patents, and other valuable business information inaccessible and threatened to be stolen, leaked, or destroyed for good. To avoid the doomsday, i.e. having business operations put to a standstill, damaged reputation, loss of clients, tiresome legal battles, and huge fines, some organizations are left with no choice but to pay ransom to get the decryption key.”
However, not many businesses can afford paying hackers off. It is estimated that the average total cost of recovery from ransomware has more than doubled from around $761K in 2020 to $1.85M in 2021. And the most worrying fact is that paying a ransom doesn’t guarantee that you will get back what’s been taken away. There’s also no guarantee your business won’t get attacked again.
Most prolific ransomware operators
The study by NordLocker has analyzed 10 ransomware gang websites. The most prolific ransomware family is Conti, with 450 attacks under their name. REvil (210 hacks), DopplePaymer (200), and PYSA (188) are also among the most famous and active cybercrime groups that harass businesses.

The analysis has found that the top five countries where businesses get attacked most are the US (732 cases), UK (74), Canada (62), France (58), and Germany (39). According to Oliver Noble, most ransomware gangs come from the post-Soviet states, which still maintain their unfriendliness towards the US and seek to cause harm to both its private and public sectors. Also, a strong belief that American companies are all wealthy might contribute to the reason they get attacked most.
“Internationally operating law enforcement groups work hard to shut ransomware infrastructure down,” says Oliver Noble. “Just last week it was reported that a joint operation put REvil’s servers offline. However, the Russian Ransomware-as-a-Service gang is expected to re-emerge. Ransomware is no longer what only skilled hackers are capable of. Any paying user, aka affiliate with little technical knowledge, can use the subscription-based model to employ already-developed tools to execute ransomware attacks against businesses.”
How to protect your business from ransomware
Although ransomware attacks are evolving, there are some easy-to-implement cybersecurity tactics to serve your business as defense:
- Make sure your employees use strong and unique passwords to connect to your systems. Better yet, implement multi-factor authentication.
- Secure your email by training your staff to identify signs of phishing, especially when an email contains attachments and links.
- Implement and enforce periodic data backup and restoration processes. An encrypted cloud might be the most secure solution for this.
- Adopt zero-trust network access, meaning that every access request to digital resources by a member of staff should be granted only after their identity has been appropriately verified.
ABOUT NORDLOCKER
NordLocker is the world’s first end-to-end file encryption tool with a private cloud. It was created by the cybersecurity experts behind NordVPN – one of the most advanced VPN service providers in the world. NordLocker is available for Windows and macOS, supports all file types, offers a fast and intuitive interface, and guarantees secure sync between devices. With NordLocker, files are protected from hacking, surveillance, and data collection. For more information: nordlocker.com.
RELATED 31% Of US Companies Close Down After Falling Victim To Ransomware
“The latest statistics indicate that a worrying 37% of companies worldwide became victims of ransomware in 2020,” says Oliver Noble, a cybersecurity expert at NordLocker, an encrypted cloud service provider. “From Campari Group in the Food & Beverage industry to Baltimore County public schools in the Education sector, both of which became victims of ransomware last year, no business or institution can feel safe. Our analysis presents the scope of recent ransomware hacks as well as indicates which industries need to stay particularly cautious.”
Top industries hit by ransomware
NordLocker’s analysis reveals that Construction is the top industry hit by ransomware (93 victimized companies), followed by Manufacturing (86). Finance (69 ransomware cases), Healthcare (65), Education (63), Technology & IT (62), Logistics & transportation (59), Automotive (56), Municipal services (52), and Legal (49) are business areas that make the list of the top 10 industries most targeted by ransomware gangs.

Among the hacked companies discovered by NordLocker’s research, there were not only large organizations, such as a global hotel chain, an automotive conglomerate, or a world-wide clothing brand, but also small family-owned and operated businesses like an Italian restaurant or a local dental clinic.
“It is surprising how many companies still take cybersecurity for granted, ‘inviting’ hackers to exploit their vulnerabilities,” says Oliver Noble. “When successfully attacked, companies get all their employee data, customer details, client agreements, patents, and other valuable business information inaccessible and threatened to be stolen, leaked, or destroyed for good. To avoid the doomsday, i.e. having business operations put to a standstill, damaged reputation, loss of clients, tiresome legal battles, and huge fines, some organizations are left with no choice but to pay ransom to get the decryption key.”
However, not many businesses can afford paying hackers off. It is estimated that the average total cost of recovery from ransomware has more than doubled from around $761K in 2020 to $1.85M in 2021. And the most worrying fact is that paying a ransom doesn’t guarantee that you will get back what’s been taken away. There’s also no guarantee your business won’t get attacked again.
Most prolific ransomware operators
The study by NordLocker has analyzed 10 ransomware gang websites. The most prolific ransomware family is Conti, with 450 attacks under their name. REvil (210 hacks), DopplePaymer (200), and PYSA (188) are also among the most famous and active cybercrime groups that harass businesses.

The analysis has found that the top five countries where businesses get attacked most are the US (732 cases), UK (74), Canada (62), France (58), and Germany (39). According to Oliver Noble, most ransomware gangs come from the post-Soviet states, which still maintain their unfriendliness towards the US and seek to cause harm to both its private and public sectors. Also, a strong belief that American companies are all wealthy might contribute to the reason they get attacked most.
“Internationally operating law enforcement groups work hard to shut ransomware infrastructure down,” says Oliver Noble. “Just last week it was reported that a joint operation put REvil’s servers offline. However, the Russian Ransomware-as-a-Service gang is expected to re-emerge. Ransomware is no longer what only skilled hackers are capable of. Any paying user, aka affiliate with little technical knowledge, can use the subscription-based model to employ already-developed tools to execute ransomware attacks against businesses.”
How to protect your business from ransomware
Although ransomware attacks are evolving, there are some easy-to-implement cybersecurity tactics to serve your business as defense:
- Make sure your employees use strong and unique passwords to connect to your systems. Better yet, implement multi-factor authentication.
- Secure your email by training your staff to identify signs of phishing, especially when an email contains attachments and links.
- Implement and enforce periodic data backup and restoration processes. An encrypted cloud might be the most secure solution for this.
- Adopt zero-trust network access, meaning that every access request to digital resources by a member of staff should be granted only after their identity has been appropriately verified.






























