Attacks using Microsoft SQL Server increased by 56% in September 2022 compared to the same period last year. Perpetrators are still using a common attack employing SQL Server to attempt to gain access to corporate infrastructures. The technical details of one of these incidents were analysed in Kaspersky’s new Managed Detection and Response report.
Microsoft SQL Server is used worldwide by corporations, medium and small businesses for database management. Kaspersky researchers found an increase in attacks that utilise Microsoft SQL Server’s processes. In September 2022, the number of SQL servers hit amounted to more than 3,000 units, growing by 56% compared to the same period last year. These attacks were successfully detected by Kaspersky Endpoint Security for Business and Managed Detection and Response.
The number of these attacks have been increasing gradually over the past year and have stayed above 3000 since April 2022, except for a slight decrease in July and August.
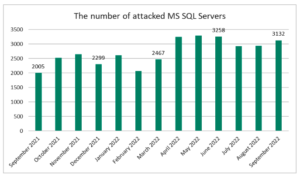
Number of attacked Microsoft SQL Servers
“Despite Microsoft SQL Server’s popularity, companies may not be giving sufficient priority to protect against threats associated with the software. Attacks using malicious SQL Server jobs have been known for a long time, but it is still used by perpetrators to gain access to a company’s infrastructure,” said Sergey Soldatov, Head of Security Operations Center at Kaspersky.
A peculiar incident: PowerShell scripts and .PNG files
In the new report, devoted to the most interesting Managed Detection and Response incidents, Kaspersky experts describe is an attack employing Microsoft SQL Server jobs – a sequence of commands executed by the server agent.
“Attackers attempted to modify the server configuration to gain access to the shell to run malware via PowerShell. The compromised SQL Server was trying to run malicious PowerShell scripts that generated a connection to external IP addresses. This PowerShell script runs the malware disguised as .png files from that external IP address using the “MsiMake” attribute, which is very similar to the behaviour of PurpleFox malware”, explained Mr. Soldatov.

An example of SQL jobs containing obfuscated PowerShell commands
To read the full Managed Detection and Response report, please visit Securelist.com.
To protect against threats targeting businesses, Kaspersky researchers recommend implementing the following measures:
- Always keep software updated on all the devices you use to prevent attackers from infiltrating your network by exploiting vulnerabilities. Install patches for new vulnerabilities as soon as possible. Once it is downloaded, threat actors can no longer abuse the vulnerability.
- Use the latest Threat Intelligence information to stay aware of actual TTPs used by threat actors.
- Choose a reliable endpoint security solution such as Kaspersky Endpoint Security for Business that is equipped with behaviour-based detection and anomaly control capabilities for effective protection against known and unknown threats.
- Dedicated services can help combat high-profile attacks. The Kaspersky Managed Detection and Response service can help identify and stop intrusions in their early stages, before the perpetrators achieve their goals. If you encounter an incident, Kaspersky Incident Response service will help you respond and minimise the consequences, in particular – identify compromised nodes and protect the infrastructure from similar attacks in the future.































