Staggering amounts of stolen login credentials were discovered by Kaspersky Digital Footprint Intelligence experts as they conducted an analysis in light of the Mobile World Congress 2024. Investigating the dark web market for credential theft from popular AI and gaming websites, the cybersecurity specialists found:
- Over the past three years, 34,000,000 Roblox users’ credentials (logins and passwords) were compromised with malware and leaked on the dark web.
- In 2023, the number of ChatGPT users’ stolen credentials increased 33-fold compared to the previous year, as 664,000 records with logins and passwords were posted on the dark web.
- Credentials in question were stolen using infostealers, specialised malware designed to steal user logins and passwords that infects personal and corporate devices through phishing and other methods.
The sale of compromised login credentials occupies a significant part of the dark web market. Cybercriminals typically buy and sell accounts from various online platforms and services. These accounts are often initially stolen using data-stealing malware and then leaked on the dark web via infostealer log-files, where they can be further monetised as valuable assets within the realm of cybercriminal activity.
RELATED: Kaspersky uncovers how scammers are using deep fake videos and fraudulent apps to lure global investors
Kaspersky has conducted research on the trends within this market and offers insights on how businesses and individuals can safeguard against the corresponding threats.
AI-services’ credential thefts are a steady trend
Credentials from various AI services – image editing, translation, text tuning, chatbots, to voice generators – are being compromised due to their growing popularity. Over the past three years, for example, approximately 1,160,000 application users’ credentials (logins and passwords) from AI-powered online graphic design tool Canva were compromised with data stealing malware. Kaspersky Digital Footprint Intelligence data¹ showed these credentials surfaced on the dark web forums and shadowy Telegram channels. Another popular AI writing assistant, Grammarly, had around 839,000 user credentials stolen between 2021 and 2023.
One of the most popular AI companies, OpenAI also witnessed users’ credentials being leaked as a result of infostealer activities – nearly 688,000 ChatGPT credentials were compromised between 2021 and 2023 and found on shadowy channels. Notably, in the last year of widespread chatbot adoption, the number of logins and passwords leaked surged by nearly 33 times in 2023 compared to the previous year, reaching approximately 664,000.
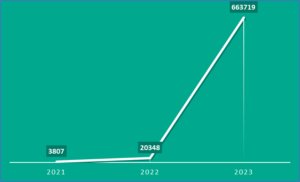
The dynamics of credentials from ChatGPT accounts compromised in 2021-2023 and leaked on the dark web. Source: Kaspersky Digital Footprint Intelligence
“The credential compromises in question stem from infostealer activity, a specialised form of malware designed to steal user credentials for cyberattacks, dark web sales, or other malicious activities. Both personal and corporate devices can be infected by infostealers through phishing emails or websites, public-faced sites with malicious content, and various other means,” says Yuliya Novikova, head of Kaspersky Digital Footprint Intelligence.
Beyond the volumes of compromised accounts outlined above, the dark web market for credentials can be analysed from the angle of demand for these accounts – specifically by examining the number of posts in which threat actors offer or attempt to buy infostealer log files containing these compromised credentials. The demand for ChatGPT accounts among cybercriminals spiked in March 2023 after the release of the fourth version of the popular chatbot. Since then, it has stabilised at the same level as other AI services. “This suggests that demand for ChatGPT accounts will remain steady. The importance of robust solutions to safeguard against infostealer attacks and other malware is growing for both individuals and companies. For instance, our solution monitors compromised accounts on the dark web and notifies companies in case users of their online resources were compromised,” explained Novikova.
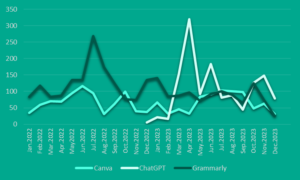
The dynamics of dark web posts selling or buying accounts from three popular AI services, 2022-2023. Source: Kaspersky Digital Footprint Intelligence
Roblox sets records for compromised credentials, posing a threat to kids
Between 2021 and 2023, almost 34,000,000 credentials for Roblox were compromised and posted on the dark web, turning the game into a very fruitful target for cybercriminals using infostealing malware. Worryingly, the number of accounts compromised for this popular children’s game have been increasing gradually each year: over the past three years, this figure rose by 231%, from roughly 4,700,000 in 2021 to 15,500,000 in 2023. In general, the average number of compromised accounts in a combination of 11 other random popular gaming platforms or games – Twitch, Electronic Arts, Sony PlayStation, and Steam amongst others – has increased by 112% since 2021.
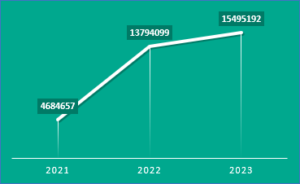
The dynamics of Roblox account compromises in 2021-2023. Source: Kaspersky Digital Footprint Intelligence
“The reason behind such high volumes of thefts of login credentials associated with Roblox is that children are among the most vulnerable audiences, as they are susceptible to various kinds of social engineering. For instance, cybercriminals can hide infostealers in files containing cheat codes to deceive young gamers. In some cases, this deception may appear genuine, as malicious download links can be posted on legitimate and popular social media platforms like YouTube. As a result, a significant number of compromised accounts have emerged from a game targeted at children,” explains Novikova.
While there are numerous cases of thefts of login credentials on Roblox accounts, they are not the primary goods cybercriminals seek on the dark web. Certain accounts are much more appealing to them: for example, the number of dark web posts selling or buying Steam accounts peaked at approximately 10,000 between 2021 and 2023, while advertisements related to stolen Roblox accounts remained under just 150.
“Criminals target game accounts to steal valuable items, such as real money, in-game currency, and various in-game items, such as expensive skins. Steam accounts seem to be more appealing to cybercriminals due to the potential to find and steal real money on them. Roblox accounts can be exploited to steal in-game currency Robux, or to pilfer in-game items, or to gain access to premium accounts that allow items to be transferred to other accounts. While users must exercise caution, platform owners can bolster protection by tracking and promptly blocking compromised accounts through specialised services”, adds Novikova.
To avoid threats related to password leaks, it is worth implementing the following security measures:
- At a company, organise a proactive monitoring of the dark web to identify account compromises before they impact cybersecurity of clients and employees. Kaspersky has compiled a detailed guide on how to set up monitoring.
- Use Kaspersky Digital Footprint Intelligence to help security analysts explore an adversary’s view of their company resources, promptly discover the potential attack vectors available to them. This also helps raise awareness of existing threats from cybercriminals so you can adjust your defenses accordingly or take timely countermeasures to eliminate threats and remedy the situation.
- For individuals, protect all the devices you use with a reliable security solution, such as Kaspersky Premium.
- Use a different password for each service. That way, even if one of your accounts gets stolen, it won’t affect the rest.
- Wherever possible, protect your accounts with two-factor authentication. Otherwise, comb through account settings.
Reference:
¹Hereafter the statistics might include duplicates, since same credentials might have been compromised several times and could have potentially been reposted on the dark web

































