Distributed Denial of Service (DDoS) attacks increased consistently in the third quarter of 2022, particularly those conducted by professionals. The number of so-called smart attacks during this term doubled compared to the same period of the last year.
Moreover, the proportion of sophisticated DDoS attempts became even more significant: while the number of attacks by hacktivists were markedly notable in the first two quarters of this year, their activity almost vanished in the third one. These and other findings are part of a quarterly DDoS report issued by Kaspersky.
RELATED: Crypto-collapse and rising smart attacks: Kaspersky reports on DDoS in Q2
A Distributed Denial of Service (DDoS) attack is designed to stop a website from functioning normally or disrupt it completely. During an attack (which usually targets government institutions, retail or financial companies, media or other organisations) the victim loses customers due to the unavailability of their website and their reputation suffers.
In Q3 2022, the number of DDoS attacks of all types rose in relation to the previous reporting period. According to Kaspersky experts, this is a standard picture: a relatively calm Summer (European) is followed by a sharp surge in DDoS activity. Moreover, compared to Q3 2021, the overall number of DDoS attacks rose by 47.87%, while the number of smart, or sophisticated and professionally conducted attacks, doubled.
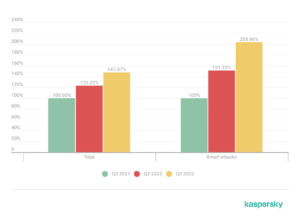
A comparative number of DDoS attacks: Q3 2022 and Q3 2021 as well as Q2 2022. Data for Q3 2021 is taken as 100%
What makes the third quarter more remarkable is the continuous drop in non-professional attacks. Although hacktivists were quite passionate and prolific in their DDoS attempts during the first half of 2022, in Q3 they switched to other malicious activity. By Q3, the number of hacktivist DDoS attacks was tending towards zero.
Meanwhile, the number of high-quality professional attacks, after a significant increase in Q1, remained at a high level. The targets have not changed either: mainly in the financial and government sectors. Both of these facts reinforce the notion that, from the Spring (European) until at least the end of September, professionals were working against these sectors, as reflected in our statistics.
In terms of DDoS attack duration, there were no new records: if Q2 was marked by the longest attack ever observed, Q3 was calmer. On average, attacks lasted about eight hours, with the longest being just under four days. Compared to the previous quarter, this figure seems rather modest, but the figures are still immense. In Q3 of last year, the duration of DDoS attacks was measured in minutes, not hours. The situation remains challenging in this regard.
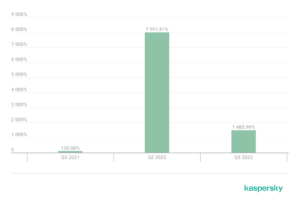
A comparative duration of DDoS attacks: Q3 2022 and Q3 2021 as well as Q2 2022. Data for Q3 2021 is taken as 100%
“Since the end of February, we have been observing and thwarting an unusually high amount of amateur hacktivist attacks. However, the number of these kinds of attacks has been gradually declining and by the end of Q3 had returned to normal levels. During this period, we observed plenty of sophisticated attacks aimed at reaching clearly defined goals: for example, to cut media outlets off, or even suspend general operations of government organisations,” comments Alexander Gutnikov, a security expert at Kaspersky.
Read more about DDoS attacks in Q3 2022 on Securelist.
To stay protected against DDoS attacks, Kaspersky’s experts recommend implementing the following measures:
- Maintain web resource operations by assigning specialists who understand how to respond to DDoS attacks.
- Validate third-party agreements and contact information, including those made with Internet Service Providers. This helps teams quickly access agreements in case of an attack.
- Implement professional solutions to safeguard your organisation against DDoS attacks. For example, Kaspersky DDoS Protection combines Kaspersky’s extensive expertise in combating cyberthreats and the company’s unique in-house solutions.
- Know your traffic. Use network and application monitoring tools to identify traffic trends and tendencies. By understanding your company’s typical traffic patterns and characteristics, you can establish a baseline to more easily identify unusual activity that is symptomatic of a DDoS attack.
- Have a restrictive Plan B defensive posture ready to go. Be in a position to rapidly restore business-critical services in the face of a DDoS attack.






























