Between January 20 and 24, the town of Davos-Klosters, Switzerland hosted the annual World Economic Forum (WEF). Among the key highlights drawing media attention were several special addresses by prominent political figures. NETSCOUT’s ASERT team of engineers and researchers specialising in information security observed an increased volume of distributed denial of service (DDoS) attacks shortly before and during at least one of these addresses. This piece chronologically follows the events of the WEF while elaborating on events in the Swiss cyberspace.
RELATED: Cyber attacks surge: Global giants face $15T threat by 2030
DDoS Attack Chronology
Between the opening and closing of the event, ASERT observed more than 1,400 DDoS attacks of varying sizes and vectors. During, and around the WEF, the observed number of attacks were approximately twice as high as comparable time periods in December. The following graphs will explore the observed DDoS attack events by day. An overview is provided in Figure 1, with the grey-highlighted vertical bars representing the Forum’s schedule.
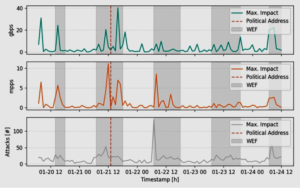
Figure 1: Three DDoS attack metrics as observed by ASERT. The grey regions mark the official schedule of the event.
DDoS attack events by the day
- January 19: Although the Forum was not set to begin until midday on January 20, ASERT detected high-bandwidth DDoS activity targeting a major Swiss service provider network. The attacks were observed between 10:50 and 12:30, peaking at 426 Gbps. The primary vector was DNS reflection amplification traffic, symptomatic for attacks aiming for bandwidth saturation. It is possible this was a preparation or reconnaissance run, and threat actors were testing the effectiveness of the chosen attack vector. To ASERT’s knowledge, the 426 Gbps attack did not cause any significant harm or outage. We will examine in future attacks that the vectors and methodology employed by attacker changed.
- January 20: The Forum’s first official session began at 14:00 UTC (15:00 local time). The opening was accompanied by high-bandwidth and throughput anomalies, that spiked at 24 Gbps during the event at 15:20 UTC. Contrary to the previous day’s attacks, the DDoS attacks leveraged various reflection amplification vectors likely in the hope of a more disruptive effect.
- January 21: As day two progressed, ASERT observed an ever-growing number of DDoS attack activity leading up to one of the speeches. The attacks feature primarily TCP-based vectors, while some smaller avalanches of attack traffic target DNS servers with query floods on UDP/53 and TCP/53. The switch to TCP-based attacks may represent yet another shift in operation from adversaries.
- January 22: The third day of the event exhibits similar patterns to the previous day, though attacks were less bandwidth saturating. TCP RST or SYN floods, along with TCP SYN/ACK amplification attacks are symptomatic for a flood of small packets, as it was observed for the day.
- January 23 and 24: Day four was relatively uneventful compared to activity of previous days. However, the closing day of the WEF coincided with notable DDoS attack activity. Even after the Forum concluded, ASERT continued to observe notable DDoS attack anomalies for several hours.
WEF in the Crosshairs of Cyber Hacktivism
DDoS attacks during high-profile events like the WEF are often indicative of politically motivated adversaries. One such actor, NoName057(16) – an actor aligned with Russian interests – is frequently associated with DDoS campaigns targeting political figures or aiming to disrupt notable events where policy discussions occur.
The group operates a notorious DDoS botnet called DDoSia, which is usually the facilitator of HTTP flooding attack traffic. However, in this instance, the adversary primarily deployed TCP-based attack methods, diverging from their usual tactics, and aligning with ASERT’s previously observed attack patterns. We show the percentage of different methods facilitated through the botnet in Figure 2.
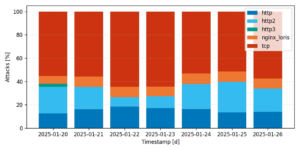
Figure 2: An overview of the DDoS attack instructions of the DDoSia botnet. Although, their signature is HTTP application layer attacks, this time the botnet primarily instructed clients to facilitate TCP traffic.
Targets of the DDoS Attacks
Figure 3 compares the industries of the DDoS attack targets in Switzerland during the WEF. It aligns with observations made during comparable events in the past – stressing again the need for resiliency and preparedness of large service providers. Often, attack traffic is directed towards service provider networks, such as telecommunication providers and cloud infrastructure. Events like these – those of international significance – also create additional stress for upstream providers.
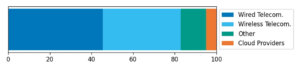
Figure 3: ASERT detangled the ~1,400 DDoS attacks and mapped the destination addresses onto their corresponding industries. It becomes clear that international assemblies primarily attract DDoS attacks that target telecommunication providers.
Conclusion
The analysis of the DDoS landscape in Switzerland highlights the importance of network visibility and sophisticated DDoS defence, such as NETSCOUT’s Adaptive DDoS Protection and curated ATLAS Threat Intelligence Feed (AIF). It underlines that service provider networks must be on alert during events of international significance.