Highlights
- Check Point Research (CPR) found a sharp increase in fake shopping related websites in the run up to Black Friday sales.
- About 17% of all malicious files distributed by email in November were related to orders/deliveries and shipping.
- Since the start of this month, 4% of all new shopping related websites have been found to be malicious.
Will November break all-time shopping records?
November is arguably the peak of the busiest shopping period, as people all over the world prepare for the holiday season. It was recently reported that over 154 million Americans shopped on Black Friday in 2021, with 88 million of them making purchases online.
RELATED: Online payment fraud increases by 208% amid the Black Friday season
According to Adobe, online holiday spending will near $210B this year, a 2.5% increase year on year. However, while consumers are getting ready to bag the best deal, cybercriminals are taking advantage of distracted minds by launching their own shopping “specials” in the form of phishing campaigns and lookalike fake websites. In this piece, we explore some of the campaigns we have seen and offer advice on how shoppers can enjoy threat-free online shopping this November.
Louis Vuitton email scam
At the end of October, Check Point researchers observed a malicious phishing email that was sent from the webmail address psyqgcg@moonfooling[.]com“ and spoofed to appear as if it had been sent from “Louis Vuitton. The email contained the subject line “Black Friday Sale. Starts at $100. You’ll Fall In Love With Prices.”. The content was designed to persuade the victim to click on two malicious links within the email, both of which redirected to the domain: “jo[.]awojlere[.]ru”. The website claimed to be selling genuine pieces of jewellery, which are in fact counterfeit, at discounted prices as part of a Black Friday sale.
The malicious links:
http://jo[.]awojlere[.]ru/return.php?p=TUsxP2pkbzh0cmFiYWpvQG9qLmdvYi5ndD80NjA4Mw%3D%3D

The well-known fashion brand was also the subject of several other fake websites. At the beginning of October, four domains with the same format were registered:
“88off-bags.co” / “87off-bags.co”/ “86off-bags.co” /“89off-bags.co”. All these websites were designed to look like the legitimate Louis Vuitton site and distributed via email with the subject – “[black Friday sale] Louis Vuitton bags up to _% off! Shop online now!” Over the past month we have seen an increasing number of visits to these domains, reaching close to 15,000 in the week of November 7th.
Delivery and shipping phishing scams
Cybercriminals are not only taking advantage of the busy buying period during the purchase process, but also at the delivery stage for those cut-price items. In the first ten days of November, we found that 17% of all malicious files distributed by emails were related to orders/deliveries and shipping.
A good example of this is a campaign of emails impersonating delivery company DHL. The emails were sent from a webmail address support@consultingmanagementprofessionals[.]com and spoofed to appear as if they had been sent from “SHIPMENT TRACKING” (see figure 1).
Attached to the email was a malicious URL https://lutufedo[.]000webhostapp[.]com/key[.]php, which aimed to steal the victim’s credentials by claiming that they needed to pay €1.99 to complete the delivery (see figure 2).
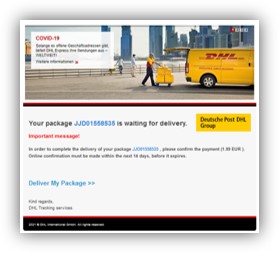
Figure 1: The malicious email which contained the subject
“[reminder]: Your package JJD01558535 is waiting for delivery. 851870943821843353”
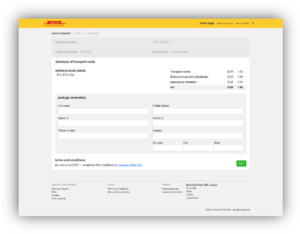
Figure 2: the malicious URL
https://lutufedo[.]000webhostapp[.]com/key[.]php
How phishing works
Phishing is a type of cyberattack where malicious actors send messages pretending to be from a trusted person or company. Phishing messages are designed to manipulate a user into performing an action, such as downloading a malicious file, clicking a suspicious link, or divulging sensitive information. The basic delivery of a phishing attack is through SMS, email, social media, or other electronic communication means.
A phisher may use public channels, such as social media networks, to collect background information about their target. These sources are used to gather details such as the target’s name, job title, and email address, as well as interests and hobbies. The phisher can then use this information to create a personalised spam message.
In a phishing campaign, the emails that the target receives will appear to come from a known contact or organization. Attackers often set up fake websites that resemble a trusted entity like the target’s bank, workplace, or university. Through these sites, attackers attempt to collect private information such as usernames and passwords, or payment information.
Some phishing emails can be easily identified due to poor copywriting or improper use of fonts, logos, and layouts. However, many cybercriminals are becoming more sophisticated at creating authentic-looking messages, and are using professional marketing techniques to test and improve the effectiveness of their emails.
Avoid the scams and enjoy threat-free shopping this November
Cybercriminals are taking full advantage of the holiday spirit. That is why it is important that everyone takes extra precautions to enjoy a safer online shopping experience. Here are six ways you can stay safe this Black Friday:
- Always buy from an authentic and reliable source: Before making a purchase, it is important to authenticate the site we are using to make the purchase. So, instead of following a link sent through on email or text message, go directly to the retailer by searching for them on your selected browser and locating the promotion yourself. Those extra few steps will ensure you are not clicking on any fraudulent links, and you can make your purchase with confidence.
- Be alert to similar domain names: Many scam websites will often use a domain name like the brand it is trying to replicate, but with additional letters or misspellings. To ensure that you are not handing over your banking information to scammers, pay attention to the URLs, is there anything usual or unfamiliar? By taking a minute to look for signs that a website may be fraudulent you can quickly identify its legitimacy.
- Look for ‘too good to be true’ offers: Often phishing scams promise extremely good discounts on very popular items. If you receive an offer that does appear to be too good to pass up, don’t rush to buy it before it sells out as chances are, it is a scam. Instead, verify that the seller is authentic by checking other websites to see if they are offering similar discounts.
- Always look for the padlock: A quick way to see whether a website is secure is to look at whether the URL start with HTTPS. This is an indicator it is compliant with international security standards, and it is usually accompanied by a padlock to reflect this. An absence of these signs could indicate that it is untrustworthy and should be avoided.
- Use endpoint security: While we do see an uplift in scam emails during popular shopping periods, phishing emails are used by cybercriminals all year round. That’s why everyone should be looking to implement email security solutions to prevent them landing in our inboxes in the first place.
- Be wary of password reset emails: With many getting their baskets ready and loading their payment information onto their accounts to make check out faster, hackers will also be looking for ways into people’s shopping accounts. As a result, consumers should be cautious of password reset emails that could be fraudulent. If you do receive one, always visit the website directly (do not click on the links) and change your password.
The statistics and data used in this report present data detected by Check Point’s Threat Prevention technologies, stored and analyzed in ThreatCloud. ThreatCloud provides real-time threat intelligence derived from hundreds of millions of sensors worldwide, over networks, endpoints and mobiles. The intelligence is enriched with AI-based engines and exclusive research data from the Check Point Research – the intelligence and research Arm of Check Point Software.
































